In addition to connected data and better insights, interoperable edtech solutions can improve your cybersecurity
School district tech directors and IT staff know that K-12 data security and privacy are growing issues. Cyberattacks and threats continue to make headlines and disrupt learning. We’ve all read reports of the 2022 cyberattack on a provider of student-tracking software that impacted the personal information of over one million current and former students in dozens of districts, including New York City and Los Angeles districts, among others.
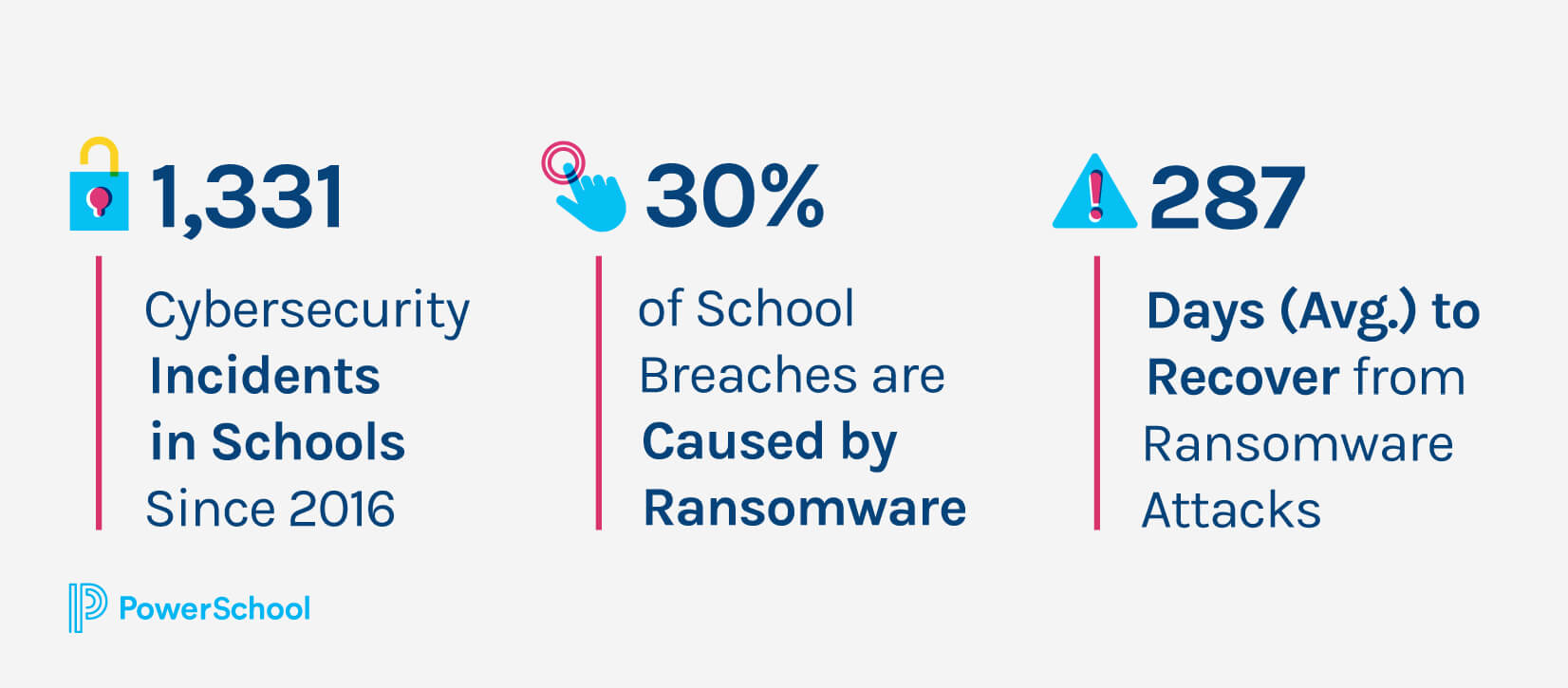
According to the K-12 Cybersecurity Resource Center, since 2016, there have been 1,331 incidents. And there’s no single type of threat to focus your efforts on. Instead, attacks come from a mix of ransomware, phishing, and distributed denial-of-service (DDoS) attacks, and unauthorized disclosures, breaches, or hacks resulting in the disclosure of personal data.
Though there’s no single threat, ransomware attacks are one threat that is emerging as especially costly. In 2021, 30% of school breaches were ransomware, affecting 954 schools and colleges. Ransomware is now “the most common type of publicly disclosed cyber incident at U.S. schools,” according to the K-12 Security Information Exchange. The fallout from ransomware attacks on your district can be devasting, with recovery lasting an average of 287 days, “even when the victim organization believed it had secure backups in place prior to the attack,” according to the IST Ransomware Task Force.
K-12 tech directors can’t eliminate threats or make their districts 100% safe, but they can take steps to improve data security and privacy. As part of your security strategy and cybersecurity awareness training, implementing interoperable edtech products can improve your data security and student data privacy.
According to Digital Promise, “School districts are often overwhelmed by managing the universe of data collected in the ever-increasing number of tools leveraged by their teachers in compliance with regulations from the federal to district level… In order for systems to maintain security, they must be interoperable.”
Here are the five ways interoperability can improve your data security and student data privacy.
Decrease Vulnerability Because All Data Remains on The Same Platform
The League of Innovative Schools defines interoperability as “the seamless, secure and controlled exchange of data.” Without interoperable products, you’re left managing the exchange of data between different vendors and platforms. Each has varying levels of security, best practices, and policies for student data privacy, adding to increased vulnerabilities for your student data.
An interoperable system offers tech directors and IT administrators greater security as data isn’t jumping from one system to another. There’s no need to export data or distribute it in unsafe ways, including manual processes or open exchanges.
Create a More Controlled Environment
With interoperable edtech products, user permissions can be adjusted for various roles to make sure you’re granting access to only those staff who need it. By limiting access to specific, known users, you can also ensure accountability. With one account and login, it’s easier for department heads and senior personnel to drill down into transactions to verify they’re appropriate.
Permission restrictions reduce the likelihood that a rogue employee or student can cause damage by accessing a database or program they shouldn’t. A recent EdTech Magazine article points out that students are a growing perpetrator of DDoS attacks, which can halt districts’ ability to perform functions online.
“While in some instances the disruption is perpetrated by professional threat actors, schools are increasingly finding their own students are behind these DDoS attacks,” says author Rebecca Torchia.
Simplified Processes Reduce Security Risks
Interoperable systems are often built with single sign-on (SSO) technology. Instead of using different usernames and passwords for each program, single sign-on gives users access to all software with just one login. This goes a long way toward preventing passwords from getting into the wrong hands.
Single sign-on also reduces the need to write down passwords, which presents major security risks. A compromised user is someone who doesn’t mean to cause problems, but whose systems have been infected or login credentials stolen. The majority of data breaches are caused by weak or stolen passwords.
“The convenience of having everything in one place keeps us from the agony of logging into as many as 18 different platforms with multiple passwords,” says Jeannette Johnson, former Director of SIS Integration and Data Quality at South Carolina’s Georgetown County School District.
Another security benefit of simplifying processes is through an interoperable set of products’ integrated design to improve usability and overall efficiency. An interoperable system typically incorporates a consistent user experience with the same look and feel, font size and type, menu dropdowns, and navigation for each product. With a consistent interface, users are more likely to understand how to use the product itself. Proper use of software supports security best practices and allows the vendor to better control back doors and other protocol interfaces that can lead to vulnerabilities within the product.
Make Account Management More Consistent
With fragmented software, you can apply only the account management solution that’s compatible with each individual program.
In comparison, it’s easier for tech leaders to maintain consistent, comprehensive security best practices for user account management when using innovative, integrated technology and role-based permissions. For example—as another benefit of SSO—your district can plug in a top-tier password management solution and use it across all participating applications.
Log Out One Time
In an integrated system, when you log out of a single product, you automatically sign out of every program. This is handy for K-12 administrators using multiple products who step away from their computers briefly.
With single logout, you don’t have to worry if someone forgets to sign out of all programs when they leave their desk, leaving their systems open to an unauthorized user gaining access. It also gives administrators the control to reboot the entire platform or log everyone off at the same time, if needed, especially in the case of an emergency.
How PowerSchool’s Interoperable, Integrated Solutions Improve Data Security
PowerSchool features interoperable solutions for use throughout K-12 operations—from the office to the classroom to the home. PowerSchool’s integrated solutions provide a seamless, secure, and controlled exchange of data to help you improve student outcomes, teacher effectiveness, and operational efficiency.
PowerSchool

PowerSchool treats every account as a precious information asset.
Rich Gay Chief Information Security Officer
PowerSchool
We’re dedicated to best-in-class security in our interoperable products, as a company, and with our employees. Initiatives to become the most progressive edtech company in the field of data security and privacy include SOC 2 Compliance, use of a Security Operations Center (SOC), and ISO 27001:2013 certification. We perform penetration testing, vulnerability scans, and next-generation endpoint protection. PowerSchool uses WAF (web application firewall) and IDS/IPS (Intrusion Detection System/Intrusion Protection system) to protect our networks and devices, and secure software development/OWASP to confirm that security is considered in the entire end-to-end process of developing software.
“As the largest K-12 edtech company, serving 45 million students, PowerSchool treats every account as a precious information asset,” says Rich Gay, PowerSchool’s Chief Information Security Officer. “We have the right security professionals, we have scale, and we want to take the discipline of data security even further.”
Additional company-wide and product security practices and activities include:
- Signatory of the 1Edtech Standards First Pledge, showing a commitment to building interoperable software while adhering to rigorous and third-party-validated open standards. PowerSchool’s products have been vetted and accredited by 1EdTech (Formerly IMS Global) as a TrustEd App. TrustEd Apps gives K-12 institutions and suppliers a helping hand to reduce the time and worry spent determining whether a particular edtech tool meets today’s expectations in data privacy.
- Signatory of the national Student Privacy Pledge regarding the collection, maintenance, and use of student personal information.
- Privacy, security policies, and infrastructure are tested and validated continually by credible industry-leading third parties and align with state and federal regulations.
- PowerSchool Connected Intelligence K-12 is the first fully managed data as a service platform, which secures all your school or district data in one location thanks to PowerSchool’s partnership with Snowflake via the Powered by Snowflake program. Having ownership of and access to all data in one place empowers educators and stakeholders with critical insights to improve student outcomes.
Final Key to Data Security and Privacy
As the use of digital recordkeeping and online learning continues to grow, it’s likely that both cybersecurity threats and attacks will also rise. As a tech director, the key is to take a comprehensive approach to ensure your valuable data is as safe as possible. In addition to your internal strategies and best practices, this approach also involves improving your human firewall, your culture of data protection, and your edtech products.
Choosing interoperable software solutions is a fundamental piece of that strategy. By doing so, you can rest assured that your data is transferred between your products as safely and securely as possible.
Improve Workflows with Interoperable Edtech
Visit our Interoperability and Security page to learn more benefits of an integrated, secure system for your students, staff, schools, and entire district.
Learn More